How to reset the Domain Admin Password under Windows 2003 Server
Update - March 2006
I first wrote this article around 2004, and the trick was working fine on a classic pre-SP1 Windows 2003 Server. People have reported that it also works when SP1 is installed. So I assume they are right since I have not tested it on this configuration. Some people also reported that the 'net' command should be used with the flag '/DOMAIN'. Once again I have not tested it. And to be honnest my server now runs Linux so I may not be up to date with the latest patches/novelties from Microsoft. But you can still send me a mail but I may just repeat what is written above he he...
Sķb
Abstract
I have recently installed a Windows 2003 Server at home and I set up a local domain using Active Directory features. Everything worked fine until I changed the Domain Admin password. It seems that I mistyped the new password twice (which I would attribute to the previous heavy night out), and, well, I could not log on the Domain Controller anymore (I did not have a backup admin account, I do now!).
A few tricks about resetting the Domain Admin Password on Windows 2000 Server have been published, but after Microsoft strengthened some security aspects on Windows 2003 Server, those hacks do not work anymore.
After struggling a few days, I finally managed to reset the domain account and I am going to present the trick to you in this paper.
This trick has a few important requirements, be sure you meet them before yelling at me.
This paper does NOT intend to serve any malicious sort of hackers, but just lousy administrators (like me). N.B.: This is known to work on Windows Server 2003 Standard Edition, without any service pack installed. Let me know if you have tried it on another configuration. Thanks!Requirements
These are compulsory!
You need:
1/ Local access to the Domain Controller (DC).
2/ The Local Administrator password.
3/ Two tools provided by Microsoft in their Resource Kit: SRVANY and INSTSRV. Download them from here.
The Local Administrator account is also called Directory Restore Administrator or Machine Account. The password is set at Windows installation. It is possible to reset this password using some (free) recovery tools.
The trick has been tested on a domain with a single DC. If your domain has multiple DCs, it should not matter which one you decide to use.
Let's get started
Step 1
Restart Windows 2003 in Directory Restory Service Mode.
Note: At startup, press F8 and choose Directory Restore Service Mode. It disables Active Directory.
When the login screen appears, log on as Local Administrator. You now have full access to the computer resources, but you cannot make any changes to Active Directory.
Step 2
You are now going to install SRVANY. This utility can virtually run any programs as an NT Service. The interesting point is that the program will have SYSTEM privileges (as it inheritates SRVANY security descriptor), i.e. it will have full access on the system. That is more than enough to reset a Domain Admin password. You will configure SRVANY to start the command prompt (which will run the 'net user' command).
Copy SRVANY and INSTSRV to a temporary folder, mine is called d:\temp. Copy cmd.exe to this folder too (cmd.exe is the command prompt, usually located at %WINDIR%\System32).
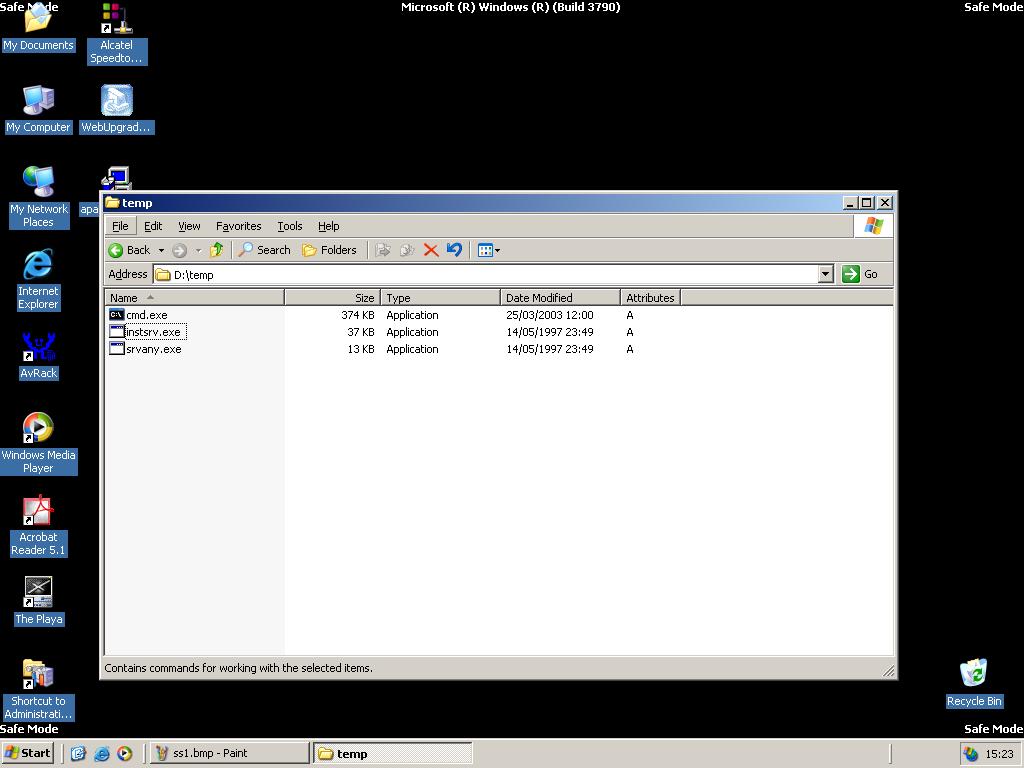
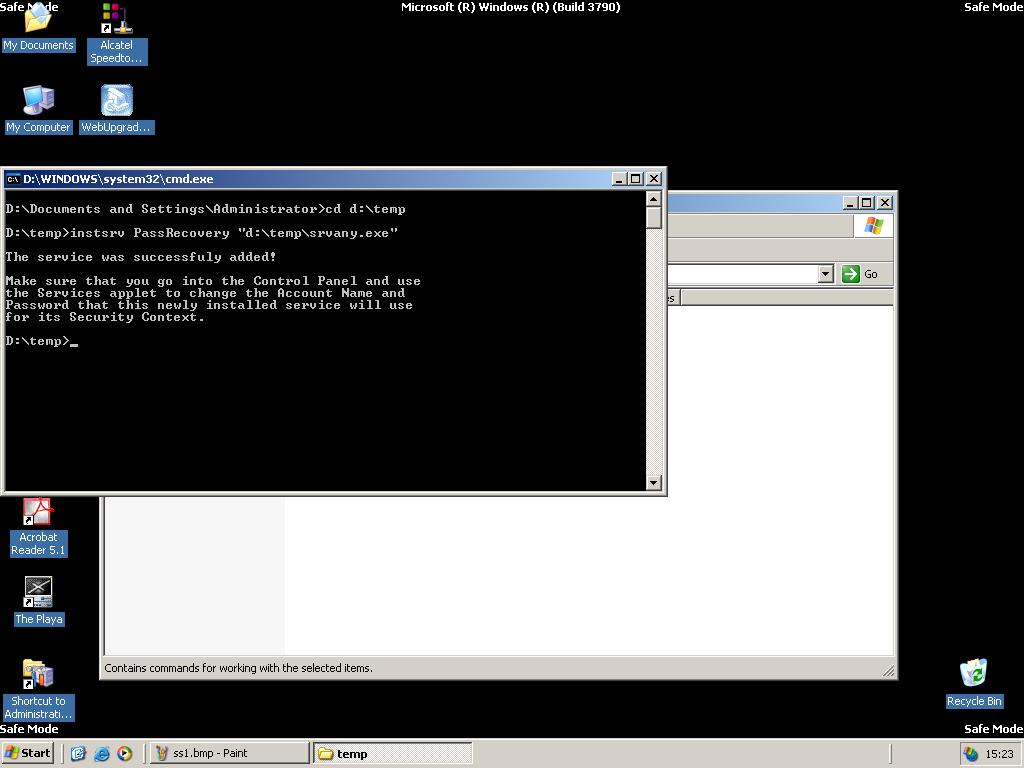
Start a command prompt, point to d:\temp (or whatever you call it), and type: instsrv PassRecovery "d:\temp\srvany.exe"
(Replace d:\temp with your folder name)
It is now time to configure SRVANY.
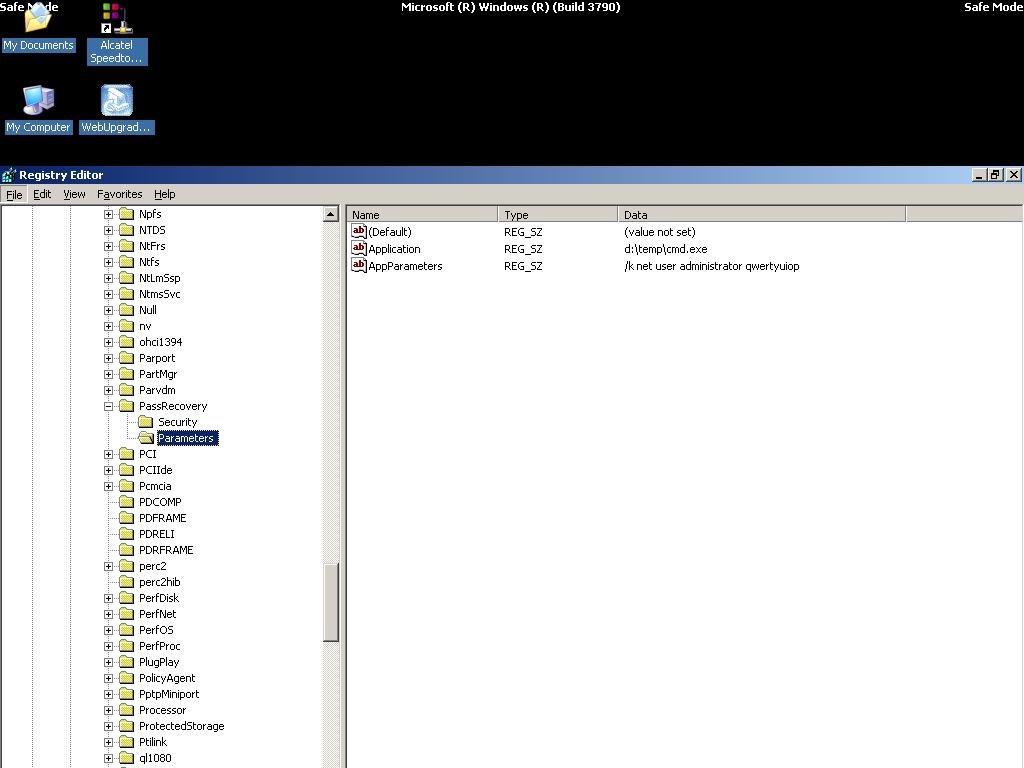
Start regedit, and open the key HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\PassRecovery.
Create a new subkey called Parameters and add two new values:
name: Application
type: REG_SZ (string)
value: d:\temp\cmd.exe
name: AppParameters
type: REG_SZ (string)
value: /k net user administrator new_password
'net user username password' is the command line utility to set a new password. Replace new_password with the password you want. Keep in my mind that some domain policies require complex passwords (including digits, respecting a minimal length etc.)
Now open the Services applet (Control Panel\Administrative Tools\Services) and open the PassRecovery property tab. Check the starting mode is set to Automatic.
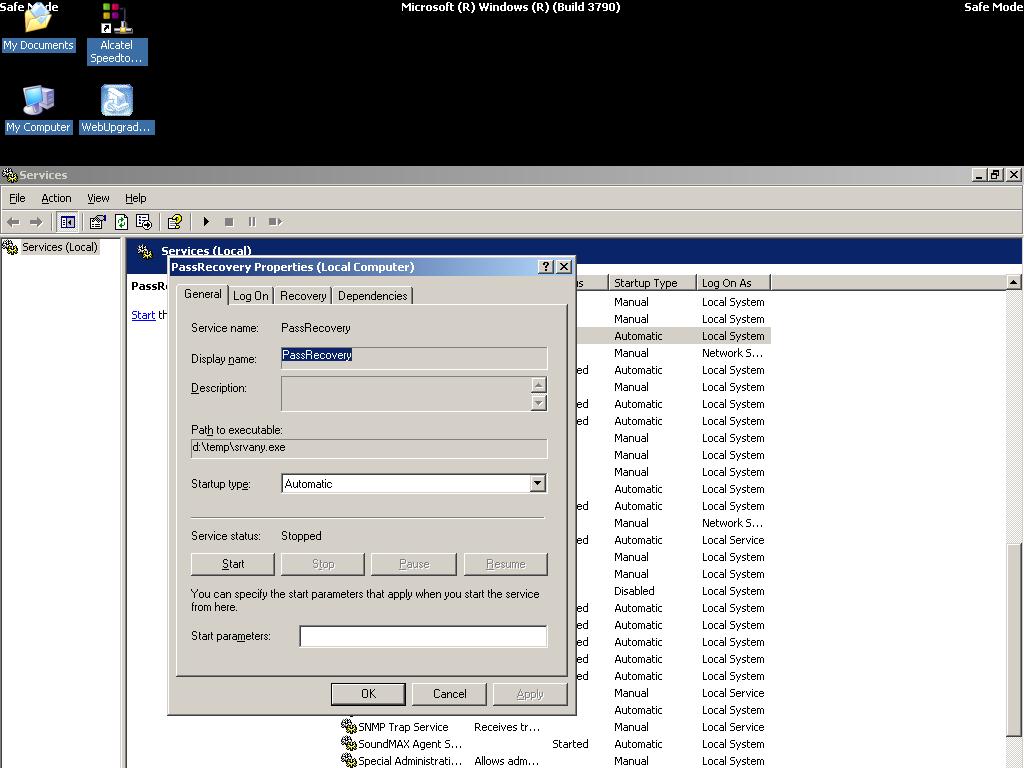
Show the Log On tab and enable the option Allow service to interact with desktop.
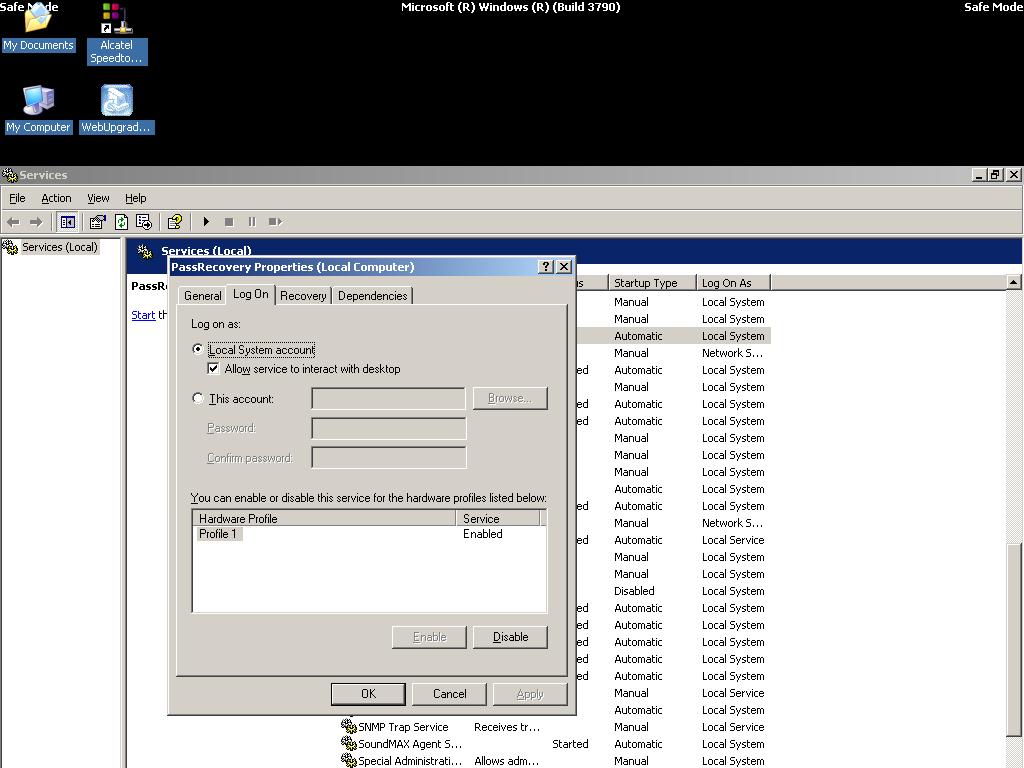
From now on, anytime you restart Windows, SRVANY will run the netuser command and reset the domain admin password.
Step 3
Restart Windows in normal mode and wait for the login screen. You will not see the command prompt running the net user command as it is displayed on another desktop. But no worries, the command is still executed in the background.
Log on as Administrator on your domain by using the password you set above. The system should grant you access. If not, go back to Step 2 and check you did not mistype any commands or values.
When the desktop is displayed, you should see a command prompt. This is the one started by SRVANY.
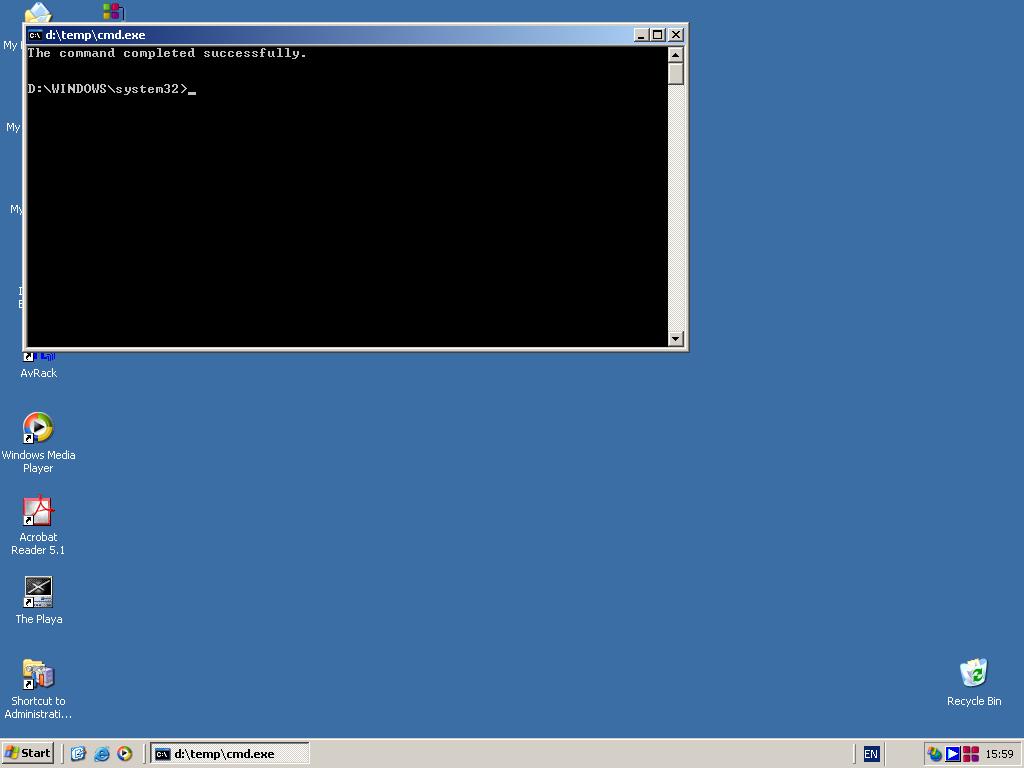
Use this command prompt to uninstall SRVANY (do not forget to do it!) by typing:
net stop PassRecovery (, then:)
sc delete PassRecovery
Now delete d:\temp and change the admin password if you fancy.
Voila!
Comments, feedback
Feel free to give me your comments and feedback. Send an email to seb@nobodix.org I will try to answer as quickly as possible.
Written by Sebastien Francois, February 2004.